Hello everyone! This blog entry is mostly for those of you that want to play with Ubuntu-Touch on the BQ Aquaris M10. You can actually purchase this tablet from BQ directly, but they have been sold out for a while, and I really wanted to have one.
So, I bought the Android version, which isn’t too different in specs. However, it comes running Android Marshmallow. I played around with it for a day just because I haven’t played with Android in a while, and realized a lot has changed since Froyo, which was the last version I played with. After the nostalgia ran off, I decided to start trying to install Ubuntu on my device.
First thing I did was go to Installing Ubuntu on Devices website. I found all the details of setting up my build machine to handle this.
First thing I did was install the ppa for the Ubuntu SDK and for the phablet-tools package.
sudo add-apt-repository ppa:ubuntu-sdk-team/ppa
Then run sudo apt update to get my repo locations updated to use the ppa.
It than install the ubuntu-device-flash which is what does all the heavy lifting and getting the image on the device. I also install adb, which is Android Debug Bridge application which is needed to manage the device and get access to the internal bits of the device, and fastboot which manages the device when its in the bootloader.
sudo apt install ubuntu-device-flash phablet-tools
After I had all the required tools on my laptop, I was ready to start. First thing I did was I had to put my M10 into Developer Mode. To do this, Click on System and go to About. Click the Build seven times. It will start a countdown on the screen saying “Press x time to enable Developer Mode.” Once done, go back and you will see Developer Options on the screen next to About. Select it and enabled OEM Unlock Bootloader, which it will bring up a prompt asking if you are sure since this does void the warranty, and it warms you every time you reboot the device saying it is in Orange State and can’t be protected and delays the boot by five seconds. Select Yes and then Enable USB Debug and turn off Protect ADB APK uploads. Probably isn’t necessary, but I did it anyways.
Now, plug your USB cable into your laptop and your device, You will get a prompt on the tablet asking if you trust this device, click the check to always trust and say Yes. You can now use the adb command on the laptop to control the tablet.
First, check that your laptop sees everything:
adb devices
You should get a return of the M10’s serial number and the word device next to it. We are now ready to go into the Bootloader. Do this from adb:
adb reboot bootloader
The device will reboot, give you the warning that I mentioned above about being Unlocked and unprotected, and then a blank screen with Fastboot Loader on the bottom. This is the fastboot bootloader. We now have to unlock the device:
Make sure you can communicate with the device with fastboot:
fastboot devices
You should get a return of the M10’s serial Number and fastboot on the same line.
You unlock the device by typing:
fastboot oem unlock
You will get a prompt on the device saying Press Volume + to Unlock and Volume – to cancel. Press Volume + on the device and you will get a confirmation saying device unlocked and on your Laptop it will say OKAY and exit. Now we can reboot the device again.
fastboot reboot
Now, it will start back up in Android, after about 10 minutes. You will have to reconfigure the device, basically I skip everything until I can get to the point where I can turn the device off. I turn it off and then I turn it back on, but when I press the power button, I also hold down the Volume + button at the same time. This will cause the M10 to go into Recovery Mode. Once The Screen comes up saying Powered by Android and you get the Unlocked Warning again, you can release the power button, but keep pressing the Volume + button until you get the Fastboot screen. Verify you can communicate to the device:
fastboot devices
You should get the serial number and fastboot on the same line. Now we can install Ubuntu….kind of.
First, you need to download the recovery image from Ubuntu since the built in one on the device does not allow adb. Depending if you have the M10 FHD or just the M10, you need a specific image. Since I was using the FHD, I need the frieza image. You can download them by clicking the appropriate link from this page.
Run the following to start the process:
ubuntu-device-flash -v touch \
--channel=ubuntu-touch/stable/bq-aquaris-pd.en \
--device=frieza --bootstrap \
--recovery-image=recovery-frieza.imgIt will download and start copying all the required files for the device. Unfortunately, it will fail. The Android partition layout is way to small for Ubuntu recovery. So, after it fails, you can wipe the cache from the device. Next, you will use adb to manage the partitions.
First, you need to download parted for Android. Luckly, I have a version here you can use. Download this and untar it and then move it to the /sbin directory on your device:
tar xf parted-android-32.tgz
adb push parted /sbin
adb shell chmod +x /sbin/partedNow we are ready to do some “damage” to the device.
NOTE: Word of caution here. We are going to delete and grow 3 file systems on the device. Please follow these directions closely and watch out for typos. You don’t want that otherwise we have to start all over again.
First, run adb shell. You are now on the console of the device as root. If you run df -h you’ll notice that /cache is out of space, and it’s only a little over 400MB in size. No where near the size we need since we have a little over 870MB of files we need to upload before we can install Ubuntu. The other thing you’ll notice once we get into the partitioning, is that the /system directory is only 1.5GB in size, and Ubuntu needs at least 4GB for the installation. However, the userdata partition is 15GB in size, so we are going to steal from there to repurpose to these other partitions.
First thing to do is run parted /dev/block/mmcblk0
Type p to list the partitions, there are 24 partitions. We are only concerned with 21, 22, and 23. First change the unit to bytes, unit b and then run p again to get that readout:
p
Model: MMC 016G70 (sd/mmc)
Disk /dev/block/mmcblk0: 15758000128B
Sector size (logical/physical): 512B/512B
Partition Table: gpt
Number Start End Size File system Name Flags
1 524288B 3670015B 3145728B proinfo
2 3670016B 8912895B 5242880B nvram
3 8912896B 19398655B 10485760B protect1
4 19398656B 29884415B 10485760B protect2
5 29884416B 80216063B 50331648B persist
6 80216064B 80478207B 262144B seccfg
7 80478208B 80871423B 393216B lk
8 80871424B 97648639B 16777216B boot
9 97648640B 114425855B 16777216B recovery
10 114425856B 120717311B 6291456B secro
11 120717312B 121241599B 524288B para
12 121241600B 129630207B 8388608B logo
13 129630208B 140115967B 10485760B expdb
14 140115968B 141164543B 1048576B frp
15 141164544B 146407423B 5242880B tee1
16 146407424B 151650303B 5242880B tee2
17 151650304B 153747455B 2097152B kb
18 153747456B 155844607B 2097152B dkb
19 155844608B 189399039B 33554432B metadata
20 189399040B 201326591B 11927552B custram
21 201326592B 1811939327B 1610612736B ext4 system
22 1811939328B 2256535551B 444596224B ext4 cache
23 2256535552B 15616966655B 13360431104B userdata
24 15616966656B 15757983231B 141016576B flashinfo
Note the start and ends for the partitions 20 and 24. Partition 21 will start with 201326592 which is +1 from the end of the previous partition. We need to do this for each partition we are growing so that they are uniform and not overlapping and cause problems.
First we need to delete the three partitions:
rm 21
rm 22
rm 23Now we are ready to recreate them, only larger in size. Since we are using bytes, the numbers are quite large, and need to equal logical sizes. Basically, do the math of starting byte, add the amount of more space you want, make that the end byte, then the next partition starts on the +1 of the last end byte until you get to partition 23, which you will end -1 byte of where partition 24 starts. So partition 23 will end with 15616966655. If you use the values that I did, you will end up with a system partition of 4.3GB, cache of 1.07GB, and a userdata of 9.6GB:
mkpart primary 201326592 4496294399
mkpart primary 4496294400 5570036224
mkpart primary 5570036736 15616966655
name 21 system
name 22 cache
name 23 userdata
quitWe now need to format the volumes:
mke2fs -t ext4 /dev/block/mmcblk0p21
mke2fs -t ext4 /dev/block/mmcblk0p22
mke2fs -t ext4 /dev/block/mmcblk0p23Now, on the device, use the Volume – to select reboot into bootloader and press the Power button to select it. The device will reboot and you will be brought back to the screen where it just says FASTBOOT on the bottom.
Now we can start the flash again, and this time it will work:
ubuntu-device-flash -v touch \
--channel=ubuntu-touch/stable/bq-aquaris-pd.en \
--device=frieza --bootloader \
--recovery-image=~/frieza-recovery.imgOnce the installation is done, you will have Ubuntu running on your device. It takes about 10 minutes to install, but after the reboot, the initial splash screen will have the BQ logo but say powered by Ubuntu and you won’t have the annoying Unlocked Device unprotected alert any more.
Let me know in the comments if you have any issues! Happy Hacking!

 40 T-Mobile SIM card for my Ubuntu Phone. I plugged the SIM in and after going online to activate it, I had a working phone with unlimited text, calling and data. First thing I did, transfer all my contacts over to the Ubuntu Phone. Took a while since they were not in Google, so I had to convert the contacts from iPhone to Google, and then boom. I had them all.
40 T-Mobile SIM card for my Ubuntu Phone. I plugged the SIM in and after going online to activate it, I had a working phone with unlimited text, calling and data. First thing I did, transfer all my contacts over to the Ubuntu Phone. Took a while since they were not in Google, so I had to convert the contacts from iPhone to Google, and then boom. I had them all.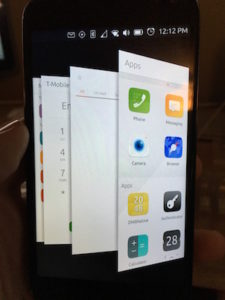 em, swipe them up (which, in my opinion, I think Apple stole from Ubuntu since they did it first… just sayin’), and then I could get to my Dock by swiping right and all my favorite apps are there, messaging, email, navigation, phone, calendar, the App Store, Scopes, which is what the main screen is on the Ubuntu phone. All my m
em, swipe them up (which, in my opinion, I think Apple stole from Ubuntu since they did it first… just sayin’), and then I could get to my Dock by swiping right and all my favorite apps are there, messaging, email, navigation, phone, calendar, the App Store, Scopes, which is what the main screen is on the Ubuntu phone. All my m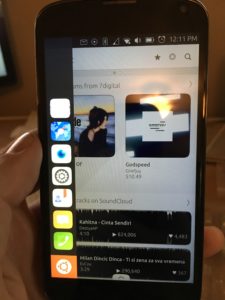 have to say, and not because I’m paid to, I actually am going to miss the Ubuntu Phone. I will still have it, and use it for testing and when I go over seas on trips since it works better then having to get a new SIM for my iPhone and having to have it unlocked for it to work, but I may actually flip for a new Ubuntu Phone when my contract with Verizon on my iPhone expires. It worked great as an emergency phone so that people could get a hold of me, and so I could keep in contact with friends and family. I’m hoping that by 2018, the Ubuntu phone matures, and hopefully will be available in the United States by a major carrier, but if not, I’ll definitely buy the phone, put a SIM in the phone and if the app doesn’t exist for it yet, I’ll build it.
have to say, and not because I’m paid to, I actually am going to miss the Ubuntu Phone. I will still have it, and use it for testing and when I go over seas on trips since it works better then having to get a new SIM for my iPhone and having to have it unlocked for it to work, but I may actually flip for a new Ubuntu Phone when my contract with Verizon on my iPhone expires. It worked great as an emergency phone so that people could get a hold of me, and so I could keep in contact with friends and family. I’m hoping that by 2018, the Ubuntu phone matures, and hopefully will be available in the United States by a major carrier, but if not, I’ll definitely buy the phone, put a SIM in the phone and if the app doesn’t exist for it yet, I’ll build it.